 Describing the datanets is not a simple thing to do, but if we start small and work ourselves up, it gets easier.
A datanet consists of many nodes. These are:
Describing the datanets is not a simple thing to do, but if we start small and work ourselves up, it gets easier.
A datanet consists of many nodes. These are:
 A data path is simply that, a path that data runs along. This can be a physical wire, a radio communication or a satellite link, it doesn't matter. Anything connected to a data path is linked to all other devices that run through data paths.
A data path is simply that, a path that data runs along. This can be a physical wire, a radio communication or a satellite link, it doesn't matter. Anything connected to a data path is linked to all other devices that run through data paths.
A data path is represented by a line.
 A user node is how a typical user interacts with the datanets. For the most part then, this means that it is a computer. A user accessing the datanets from a plug still has to be plugged into a user node. A user node can be much more than a typical computer though - it could also be the electronics of a vehicle (which accesses the datanets for time keeping, road traffic data and the like).
A user node is how a typical user interacts with the datanets. For the most part then, this means that it is a computer. A user accessing the datanets from a plug still has to be plugged into a user node. A user node can be much more than a typical computer though - it could also be the electronics of a vehicle (which accesses the datanets for time keeping, road traffic data and the like).
A user node is represented by a triangle. A user node will only ever have one data path running from it.
 A security node is usually a piece of software (although it can be a hardware device) that limits the access to what's behind it. Sometimes though, it can be used to block connections from both directions - this is sometimes useful for a corporation which restricts what data they send or recieve. Anyone without the correct passwords will be attacked by the security software here, which can be very light or incredibly heavy depending on what's being protected. Almost every link to a datanet is protected by a security node.
A security node is usually a piece of software (although it can be a hardware device) that limits the access to what's behind it. Sometimes though, it can be used to block connections from both directions - this is sometimes useful for a corporation which restricts what data they send or recieve. Anyone without the correct passwords will be attacked by the security software here, which can be very light or incredibly heavy depending on what's being protected. Almost every link to a datanet is protected by a security node.
A security node is represented by a rectangle and will have bold arrows to show the direction of unrestricted access. Any traffic that flows in the direction of the arrow will be allowed through the security node (and so will the return of that communication) but traffic that doesn't originate from the direction of the arrow will have to face whatever security the node carries. Like a user node a security node will only ever have one data path running through it.
|

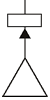
The following diagram shows a typcial household. There is a single computer (the user node) which is connected to the datanet. Protecting the computer is a security node and the the bold arrow shows that traffic can pass freely from the user node into the datanets but not the other way, meaning that if someone where to attempt to hack their way into the computer, they would have to fight whatever security measures were installed in the security node.
This setup can be used to represent many things, from a vehicles electronics to a simple connection point for a plug, a security camera, a robot brain or anything that might require its own interface.
|
 A data node is a store for information and data. Whilst individual user nodes also store information, data nodes store information that is accessable to anyone within a company or department, and as such are nearly always protected by security nodes. Datanets are full of information and this information has to be stored somewhere and data nodes are those places. Whilst most are protected by one-way security nodes (to allow for information to be passed into the public domain, but not allowing for people to post information to the node unless they have the right passwords) some are completely in the public domain and have no security. These are actually more common than people might think and are useful for the free sharing of information. Other pirate data nodes block communication from both directions meaning that only those with the correct passwords may send and recieve data to that node.
A data node is a store for information and data. Whilst individual user nodes also store information, data nodes store information that is accessable to anyone within a company or department, and as such are nearly always protected by security nodes. Datanets are full of information and this information has to be stored somewhere and data nodes are those places. Whilst most are protected by one-way security nodes (to allow for information to be passed into the public domain, but not allowing for people to post information to the node unless they have the right passwords) some are completely in the public domain and have no security. These are actually more common than people might think and are useful for the free sharing of information. Other pirate data nodes block communication from both directions meaning that only those with the correct passwords may send and recieve data to that node.
A data node is represented by a square box. It may have several data paths running to and from it, but most are connected to a minor routing node.
 A minor routing node: is a special type of node. This type of node connects other nodes together. It may have multiple data paths running through it but these may only be made up of user nodes, data nodes or other minor routing nodes. Minor routing nodes don't just allow data to be passed within offices and business, but they are also used to route data around towns, and between them. Probably the central minor routing node that allows data to leave a town will be owned by a local business or multicorp. As well as probably publicity, this also allows the owner to monitor data that passes through the node.
A minor routing node: is a special type of node. This type of node connects other nodes together. It may have multiple data paths running through it but these may only be made up of user nodes, data nodes or other minor routing nodes. Minor routing nodes don't just allow data to be passed within offices and business, but they are also used to route data around towns, and between them. Probably the central minor routing node that allows data to leave a town will be owned by a local business or multicorp. As well as probably publicity, this also allows the owner to monitor data that passes through the node.
A minor routing node is represented by a circle.
|

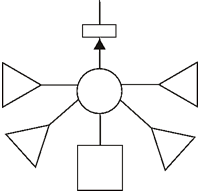
The following example shows either a small business connected to a datanet or an office connected to part of the multicorp datanet. It consists of a minor routing node which allows communcation to pass between any of the four computers and the data node (which is probably a fileserver of some sort). The connection to the datanet or the rest of the multicorp is protected by a security node.
|
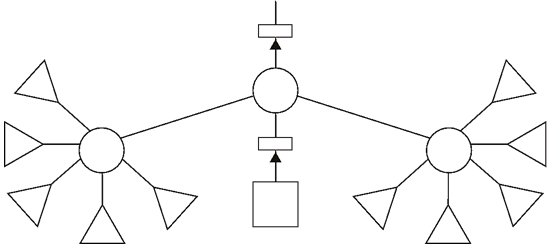
 This diagram shows a larger business. It has two offices each consisting of five computers and in addition has a protected data node. All users may share information to each other.
This diagram shows a larger business. It has two offices each consisting of five computers and in addition has a protected data node. All users may share information to each other.
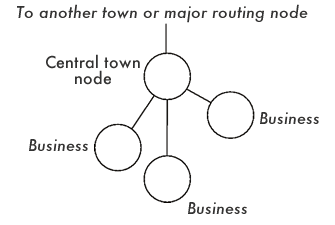
 The diagram shows how a typical town might be laid out. The town would probably have one central node which all information in and out of the town flows through. From this node the various businesses in the town would be connected. Note that there would be no users connected to the central node - they would be connected to the datanets via a local business providing this service. The town might also have its own data node providing free information to the inhabitants or those seeking information about the town. Some paranoid towns will have a security node to filter data coming into the town.
The diagram shows how a typical town might be laid out. The town would probably have one central node which all information in and out of the town flows through. From this node the various businesses in the town would be connected. Note that there would be no users connected to the central node - they would be connected to the datanets via a local business providing this service. The town might also have its own data node providing free information to the inhabitants or those seeking information about the town. Some paranoid towns will have a security node to filter data coming into the town.
If the central routing node goes down or is disconnected, then everything that links to it is now isolated and has no access to each other or to the datanets.
 A major routing node is what connects minor routing nodes together. Most cities will have at least one major routing node and these will then connect to the outlying towns. Many multicorps will have their own major routing nodes or will connect to them. Major nodes connect to each other, and this is what binds the entire datanet together. If a major node should be disconnected, then a lot of towns will lose their connection. Depending on the importance of the node, a whole portion of the country might lose their connection as well.
A major routing node is what connects minor routing nodes together. Most cities will have at least one major routing node and these will then connect to the outlying towns. Many multicorps will have their own major routing nodes or will connect to them. Major nodes connect to each other, and this is what binds the entire datanet together. If a major node should be disconnected, then a lot of towns will lose their connection. Depending on the importance of the node, a whole portion of the country might lose their connection as well.
Major routing nodes are representated by a hexagon.
Obviously the above is a very simplified description of how the datanets work, and they can get very complicated. For example, multicorps within a town might well have their own connection to the datanets which wouldn't go through the towns central routing node. Multicorps might well have their own major routing nodes with their own complicated datanet system behind high security which are not linked to anything else.
In addition, whilst the diagrams have indicated a close geographical location, this doesn't need to be the case, especially with the case of businesses. The small business diagram above might only appear to be four users and a data node, but the users might be in different towns across the country.

A typical defence against hackers might include the following. There will be
head-hunt programs in any
security nodes and there might be
patrol programs in any important
routing nodes and possibly sensitive
data nodes. Depending on the business, there might be an operator or two on stand-by ready to jack-in and actively engage hackers.
Use the Simple Set-up above, the only defence would be head-hunt software in the security node, and if the system was only for a local house hold, there might only be passwords required and not even any head-hunt software. Using the Small Business example, there would be probably be head-hunt software in the security node and maybe a patrol program in the data node which would alert operators to data jacking. Depending on the importance of the business, an operator would be around but probably not on standby, so will unlikely play any part in the hacking and instead be part of the clean-up. Important businesses will likely have an operator on standby or even working in shifts to actively move around and patrol the datanet on a 24 hour cycle.